- Blog
- 2025-07-07
- Introducing Checkpoint: A Better Way to Share Online Accounts
Introducing Checkpoint: A Better Way to Share Online Accounts
2025-07-07
I was shocked the first time I learned the US Government's official guidance for federal employees on sharing online accounts: “send an encrypted email to the recipient containing the username and password of the shared account.”
The most sophisticated cyber force on earth hasn't even heard of a password manager?
Then, it hit me: password managers are nothing more than a glorified encrypted email. It's 2025, and we deserve a better way to share sensitive online accounts. And that's exactly why we're building Checkpoint.
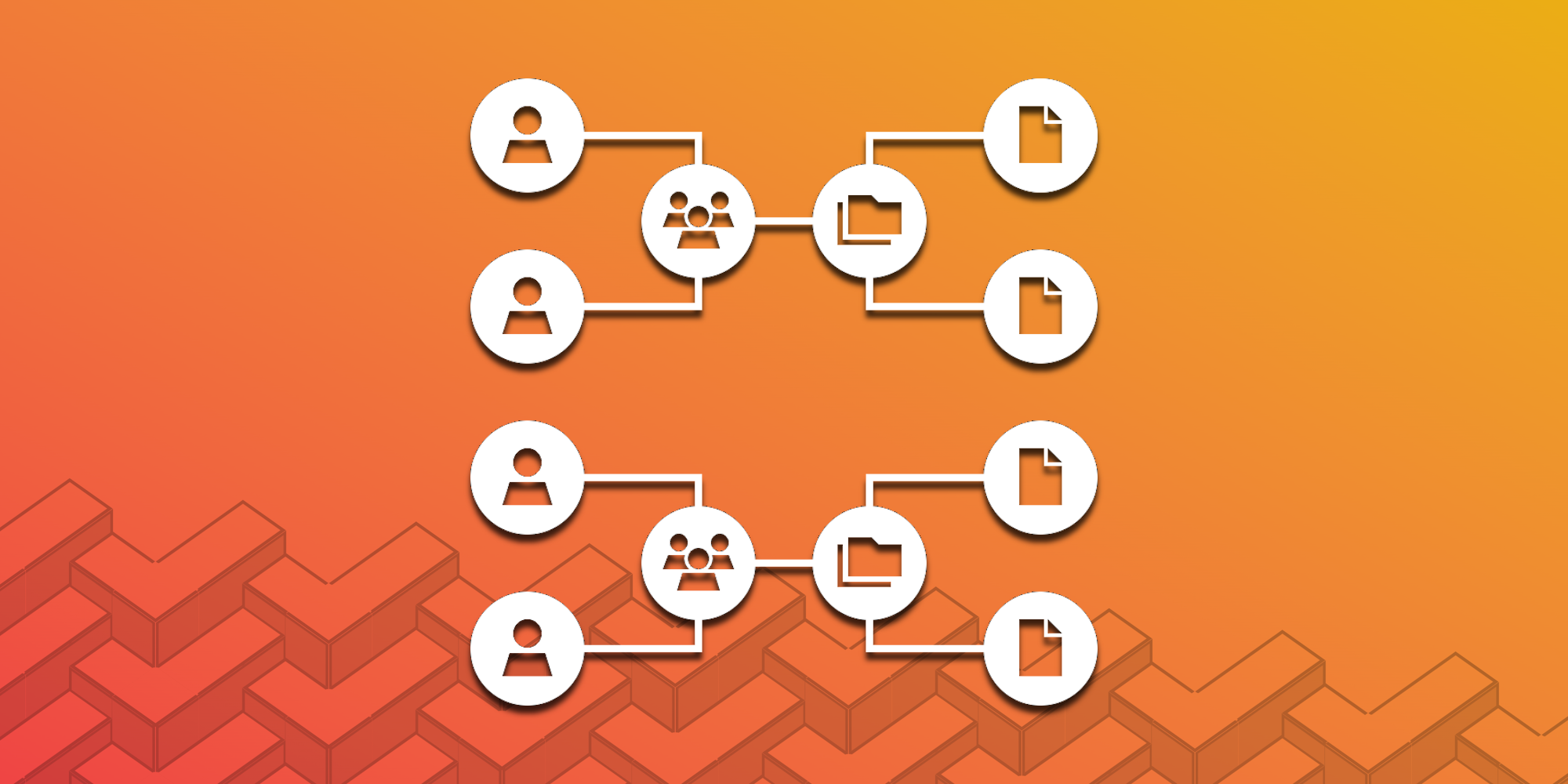
We're building Checkpoint to enable easy, secure sharing of online accounts.
Password Management Woes
Even the best password managers today have serious limitations when it comes to securely sharing online accounts.
Imagine you run an accounting team at a company, and you need to share access to an online banking portal with your team members so they can regularly monitor the latest transactions. Your credit union doesn't have built-in sharing features, and you know that your online banking credentials are sensitive, so you do the “responsible thing” and use a modern password manager to share the credentials with your team.
Irrevocable
Without knowing it, the action you just took is virtually irreversible. As soon as your credentials are available to your team members via your password manager, there's nothing stopping them from grabbing the password and writing it down on a sticky note for later use, or even sharing it with unauthorized third parties.
Now, what happens when someone leaves the team? You could go in to the password manager, find the shared account, and remove their access (giving you a false sense of security), but they've still got that sticky note, which is just as good as still having access to the password manager itself.
Sure, you could try to rotate the credential, but that's a hassle, and it's easy to forget. Each time your team changes, you would have to manually go into each shared account, update the password, and give the new password to all remaining team members. And if you've got dozens of shared accounts, this becomes a nightmare; you'd have to repeat this process for each account, any time a team member joins or leaves.
Current password managers are a slick UI on top of encrypted database; they're not designed for instant, scalable revocability.
Coarse-Grained
One morning, you log in to the shared bank account to discover a mysterious transaction. You suspect that one of your team members has far exceeded their scope, using the shared account credentials not just to monitor transactions, but also to make an unauthorized transfer.
Because password managers only allow you to share access to the entire account, they're an all-or-nothing proposition. Once you've shared the account credentials, anything the account can do, your team members can do, even if you only really needed them to be able to use one specific feature.
Repudiable
Well, at least my password manager has a “full audit log,” right? Surely I can just check the logs to see who accessed the account and when.
Unfortunately, it's time for the revenge of the sticky note. The most a password manager can do is log when a user first accessed the shared credentials, not when they actually used the credentials to access the account.
So, good luck sorting through network logs and IP addresses to figure out who made that unauthorized transfer. Let's hope they didn't take that sticky note home and use a VPN.
Weak Encryption
For some password managers, even the basic job of correctly implementing a glorified encrypted email is too much to ask. Most password managers use weak password-derived keys, which are only as strong as the master password chosen by each user. Given that most users have notoriously weak passwords, and that popular password managers have already had dozens of confirmed security incidents, what should be a vital cybersecurity resource is often turned into a massive central point of failure.
Rogue Agents
In the near future, your accounting team may be staffed by AI agents, not just humans. These agents will also need to access online accounts to perform tasks on your behalf, and will inherit all of the same security challenges as sharing accounts with humans.
What happens, for instance, when your “helpful” AI assistant decides that your online banking password is too weak, and tries to change it for you, locking you and your team out of the account?
Checkpoint: There's Finally a Better Way
We're building Checkpoint to solve the problem of securely sharing online accounts with humans and AI agents alike. Checkpoint uses novel cryptographic techniques to enable easy revocable, non-repudiable, and fine-grained sharing of any online account resource. The below video gives a quick demo of how using Checkpoint works in practice:
Video: Checkpoint uses novel cryptographic techniques to enable revocable, non-repudiable, and fine-grained sharing of any online account resource.
Revocable
Checkpoint allows you to share online accounts with your team members in a way that (a) doesn't actually expose the underlying credentials, and (b) requires all accesses to the shared account to be made via the Checkpoint system. As a result, shared access to accounts is easily and instantly revocable. If a team member leaves, you can immediately revoke their access to the shared account without having to change the password or update any credentials.
Nonrepudiable
Because all accesses to the shared account must go through the Checkpoint system, it's also easy to prove who accessed the account, when they accessed it, and exactly which actions they took. This non-repudiable access log is crucial for auditing and compliance purposes, and makes it impossible for shared account accesses to go undetected.
Fine-Grained
Checkpoint allows you to define fine-grained access controls for each shared account. You can specify exactly which team members have access to which resources, and what actions they are allowed to perform. For example, in the accounting department example, Checkpoint makes it easy to give team members “read only” access to a bank account, even if the bank itself doesn't natively support that feature. This level of granularity is essential for maintaining security and compliance in complex organizations, yet simply isn't possible in existing password management systems.
Strong Encryption
Checkpoint is also built on top of our Next-Generation Multi-Factor Key Derivation Function (MFKDF2), which securely derives cryptographic keys from multiple, commonly-used authentication factors, rather than relying on a single master password. This, combined with our soon-to-be-announced “Switchboard” technology, means that Checkpoint is already starting on a much stronger cryptographic foundation than most existing password managers, ensuring it won't become a central weak point in your identity security posture.
Agentic Access
All of the benefits of Checkpoint for sharing online accounts with humans also apply to AI agents. Checkpoint allows you to securely share access to online accounts with AI agents, via existing computer use and browser use platforms, while maintaining fine-grained control over what the agents can do. This is crucial for ensuring that AI agents can perform tasks on your behalf without compromising your security or privacy.
Behind the Scenes
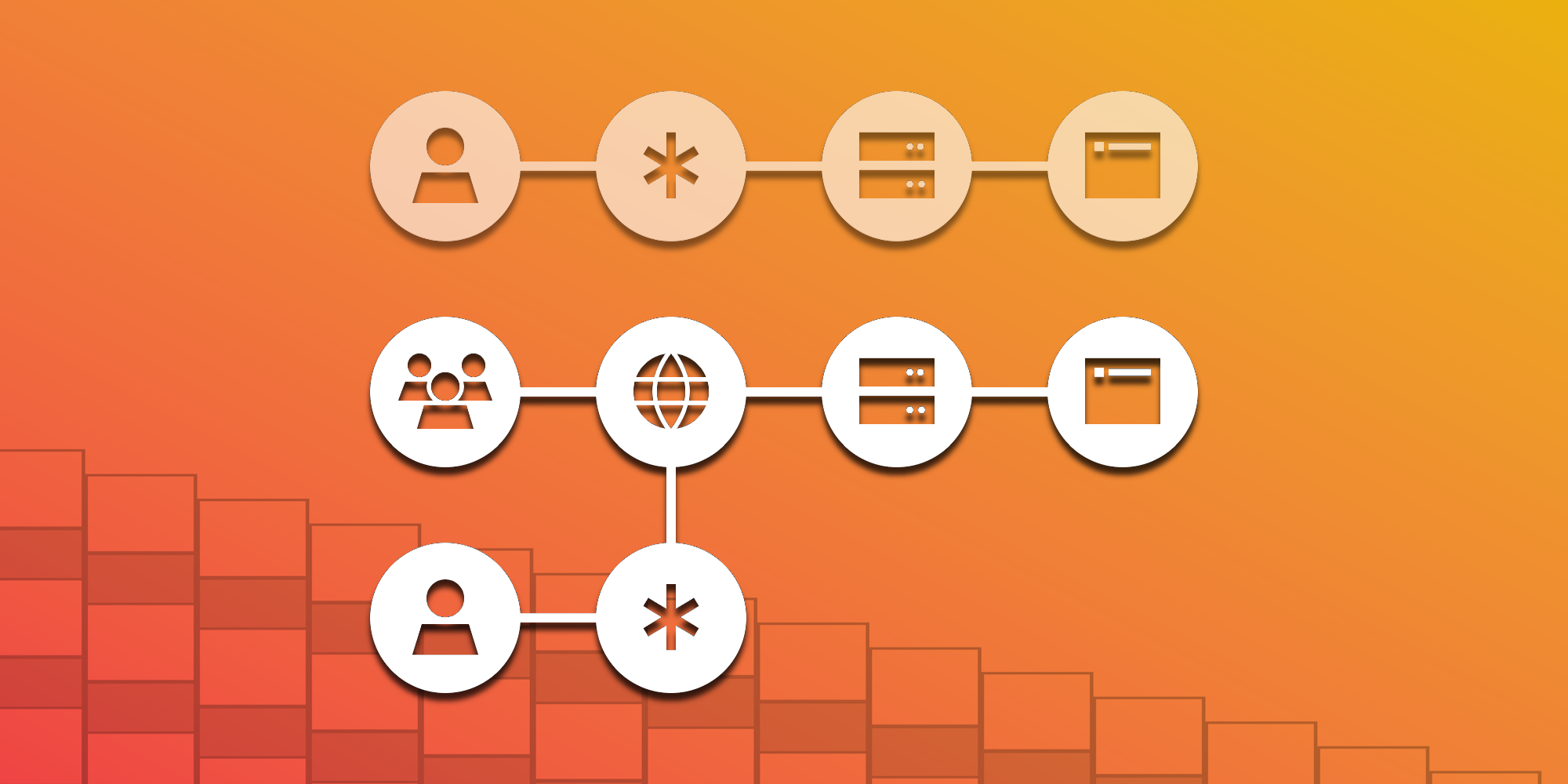
Under the hood, Checkpoint uses a proxy-based architecture to mediate all access to shared accounts. Checkpoint sits between a web service hosting a shared account and the user accessing that account, securely intercepting requests and responses to enforce the access controls defined by the account owner.
This means that no special support is required from the service being accessed, and Checkpoint can be used with any online account that supports standard authentication methods.
TEEs
Our proof-of-concept implementation of Checkpoint uses Trusted Execution Environments (TEEs), specifically AWS Nitro Enclaves, to securely mediate access to shared accounts. TEEs provide a secure enclave within the host system, allowing Checkpoint to perform sensitive operations without exposing the underlying data to the host system or any other processes running on the machine. By generating an attestation of the code running within the enclave, Checkpoint can prove to end users that their account information isn't visible to Multifactor or any other third parties.
MPC
We're also actively researching the use of Multi-Party Computation (MPC) techniques to further enhance the security and privacy of shared account access. By leveraging MPC, we can enable secure computations on encrypted data without revealing the underlying information to any party involved in the computation and without requiring trusted hardware like TEEs. This would allow Checkpoint to provide even stronger guarantees of security and privacy, while also enabling more complex access control policies.
The Path Forward
We're excited to be building Checkpoint, and we believe it has the potential to revolutionize how we share online accounts. By providing a secure, revocable, non-repudiable, and fine-grained way to share access to online accounts, Checkpoint addresses the fundamental limitations of existing password management solutions. When combined with our other technologies, like MFKDF2 and Switchboard, Checkpoint will provide a comprehensive solution for secure identity management in the AI era.
As always, if you're interested in helping to support our research, or have ideas for how it could be used in your organization, please don't hesitate to reach out. We're always looking for partners who share our vision of a more secure and user-friendly identity management landscape.
We're redefining zero-trust — so you can protect your accounts with confidence.
Identity is your first and last line of defense, and the root cause of most application security breaches. Multifactor's provably secure zero-trust solutions cryptographically guarantee that only authorized users can access sensitive data, turning identity into your greatest asset in the fight against cyber threats. Learn more about our research, or reach out to explore working together.
Related Posts
Introducing Switchboard: Provably Secure, Flexible, and Efficient Authorization
2025-07-17
Switchboard is Multifactor's secure, flexible, and efficient data authorization management solution that advances the current state of the art by cryptographically enforcing complex authorization policies.
We're Hiring
2026-03-02
Multifactor is hiring. If you are a talented engineering leader or individual contributor who cares deeply about forging the future of authentication, authorization, and auditing for the agentic era, you should probably check out our open positions.
Multifactor Versus Password Managers: Securing Capabilities, Not Credentials
2026-01-31
Say goodbye to password managers and hello to Multifactor, the world’s first true Account Manager!